Business Hours: Monday – Friday: 8.30 am to 6.30 pm Break: 1.00 pm to 2.00 pm
Saturday, Sunday & Public Holidays: Closed
PROMOSI HARI RAYA AIDILFITRI 2024






































We Specialized In
Let’s look the Interior Design of Ricoh Copier Machine…..
Ricoh Color Copier Promotion

- 35cpm A4 size (B & W And Color)
- USB 2.0 & SD CARD
- Copy , Print , Scan and Fax (Optional)
- Automatic Reverse Document Feeder
- 250 GB HDD & 1.5GB RAM
- Free : Toner, Sparepart & Service
- Free 1st time delivery and installation within Klang Valley

- 55cpm A4 size (B & W And Color)
- USB 2.0 & SD CARD
- Copy , Print , Scan and Fax (Optional)
- Automatic Reverse Document Feeder
- 250 GB HDD & 1.5GB RAM
- Free : Toner, Sparepart & Service
- Free 1st time delivery and installation within Klang Valley

- 35cpm A4 size (B & W And Color)
- USB 2.0 & SD CARD
- Copy , Print , Scan and Fax (Optional)
- Automatic Reverse Document Feeder
- 250 GB HDD & 2GB RAM
- Free : Toner, Sparepart & Service
- Free 1st time delivery and installation within Klang Valley



- 55cpm A4 size (B & W And Color)
- USB 2.0 & SD CARD
- Copy , Print , Scan and Fax (Optional)
- Automatic Reverse Document Feeder
- 250 GB HDD & 2GB RAM
- Free : Toner, Sparepart & Service
- Free 1st time delivery and installation within Klang Valley



- 35cpm A4 size (B & W And Color)
- USB 2.0 & SD CARD
- Copy , Print , Scan and Fax (Optional)
- Automatic Reverse Document Feeder
- 250 GB HDD & 2GB RAM
- Free : Toner, Sparepart & Service
- Free 1st time delivery and installation within Klang Valley



- 55cpm A4 size (B & W And Color)
- USB 2.0 & SD CARD
- Copy , Print , Scan and Fax (Optional)
- Automatic Reverse Document Feeder
- 250 GB HDD & 2GB RAM
- Free : Toner, Sparepart & Service
- Free 1st time delivery and installation within Klang Valley
**Terms and Conditions Apply**
Our services
Copier Malaysia | Copier Selangor | Copier Kuala Lumpur | Copier Klang Valley | Copier Rental | Copier Service | Copier Maintenance | Copier Machine | All in one Copier | Ricoh Copier |
We deliver a complete customer experience, transcending beyond a mere office printer.
Our commitment lies in discovering the ideal office printers that align with your workspace. With a track record of over three decades, we have furnished Selangor offices with prompt and dependable printing solutions.
EXPERIENCED STAFF
Our entire team of technicians possesses a minimum of 15 years' experience in repairing office printers.
LARGE INVENTORY
We maintain an inventory of over 100 machines, primed for your installation needs. Our stock includes a comprehensive range of toners, drums, and other consumables specifically for Ricoh equipment.
ONGOING CARE
Our service agreement at copier.com.my encompasses both maintenance and repair services for office printers.
OVER 30 YEAR EXPERIENCE
For more than three decades, we have been delivering swift and dependable printing solutions to offices in Selangor.
PROMPT SERVICE
Our technicians are ready to respond to service calls for repairs and toner refills on the same day.
TAILORED SOLUTIONS
We offer a customized model and payment plan designed to suit the specific requirements of your office printer.
Control Print Speed
Cost-Effective Photocopier
Flexible Leasing Options
Full Maintenance & Support
High Quality Photocopiers
Optimize Fleet Of Print Devices
Order, Deliver & Install All Toners
Reduce Excess Printing
Reduce Your Total Print Spend
Repair All Print Devices
IT Support Hotline
Whatsapp 018-299 6296 or email us at it@bizcopier.com.my for any inquiry regarding IT problem.
Or do you interested in our 1 year unlimited remote support package? Contact us!
Service Area Covered
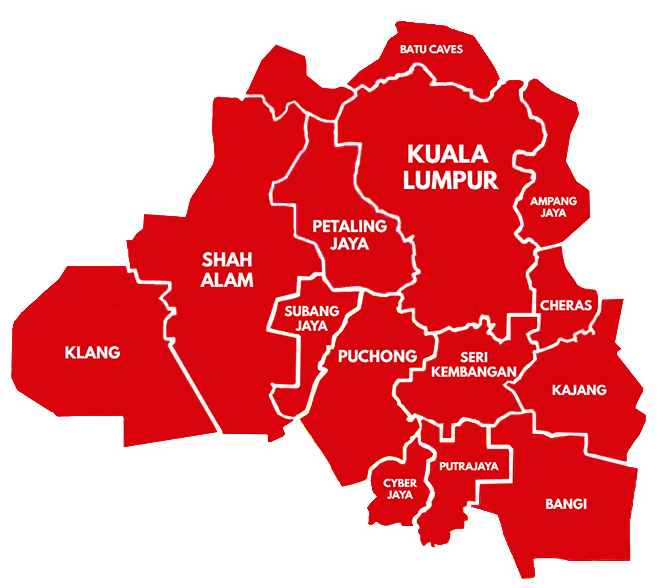
In just a minute, you can send us a request and we will send you through a proposal to meet your needs. Simply answer the few questions below and press SEND – we will calculate our best price and get back to you quickly.
Partner with US
We are constantly looking for partner to collaborate or join our business.
WhatsApp us below to discuss further.














